Table of Contents
OMNeT++/INET Packetdrill
Packetdrill in INET consists of
- Node (src/inet/node/packetdrill/PacketDrillQuicHost.ned)
- Tests (tests/packetdrill)
- Application (src/inet/applications/packetdrill)
With a Packetdrill test script, it is possible to check the content and the time of packets a host sends. The expected behavior is described in the script (in a line with “>”). To trigger outgoing packets, a test script can contain system calls and inject a packet described in the script (in a line with “<”).
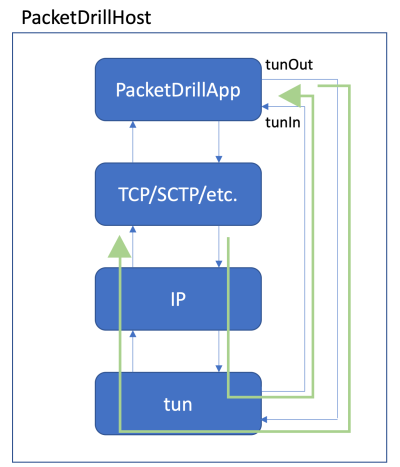
Node
The PacketDrillQuicHost node uses a tun interface to capture outgoing packets and to be able to inject generated packets. A tun interface has a direct connection to the App. The green arrows in the following figure show the packet flow.
Tests
The packetdrill directory under tests has a subdirectory for each protocol to test (e. g. quic). Inside one of these subdirectorys, There are .test files that are similar to a omnet.ini file, a runtest script to run packetdrill tests from a terminal, and a subfolder (e. g. quictests) containing the packetdrill tests scripts. Before the runtest script is able to run a test, INET needs to be built in debug mode. In INET root directory, run
$ make MODE=debug -j3
After that change to the packetdrill protocol test folder (e. g. tests/packetdrill/quic) and execute all tests with
$ ./runtest
or a specific test with
$ ./runtest quicOpenClose.test
The runtest script links against the debug version of the INET library (libINET_dbg). The output of this command shows the result. For more detailed logs, see work/quicOpenClose/test.out for stdout or work/quicOpenClose/test.err for stderr output.
Application
The packetdrill app parses the packetdrill test script file, generates events for each line (like run system call or inject packet) and executes these events.
Packetdrill uses bison as parser. The syntax is specified in parser.y and constants are specified in lexer.l. parser.y uses functions from PacketDrill.h to generate the described packets in the packetdrill test script, while parsing it. Each line results in an object of the class PacketDrillEvent. Thus, parsing a packetdrill test script results in a list of PacketDrillEvent objects. A PacketDrillEvent is either a packet event (inject packet “<”, expect outbound packet “>”), a syscall event (socket, connect, etc.), or a command event. Run
$ ./generate_parser
to generate C++ code (parser.cc, parser.h, and lexer.cc) from parser.y and lexer.l.
The PacketDrillApp uses the list of events generated by the parser and execute these events. * syscall event (e. g. connect) - Runs the equivalent of the described syscall (e. g. calls the connect method on the socket). * inbound packet event (“<”) - Uses the generated packet by the parser and sends it via tunOut interface. * outbound packet event (“>”) - Uses the generated packet by the parser and compares it to a real outbound packet captured from tunIn interface. If no real packet was sent or if the real packet differs from the generated packet, the packetdrill test fails.